Uncrackable2
This android challenge is the second one of a series of challenges offered by OWASP Mobile Application Security.
Make sure to check the writeup for the first one here, as some of its elements will be referred to and will lack of details in the current writeup : Uncrackable1
Understanding the app
This app is pretty much like the first one.
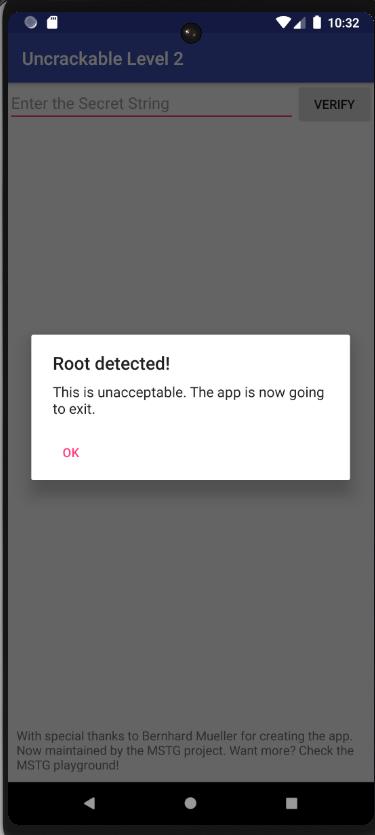
The same text field is awaiting for our secret string behind an anti-root wall.
Let’s dissect the app under Jadx :
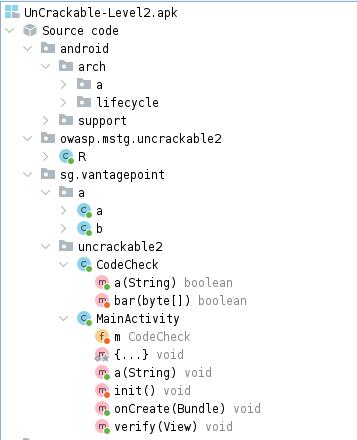
Once again, MainActivity is the entrypoint.
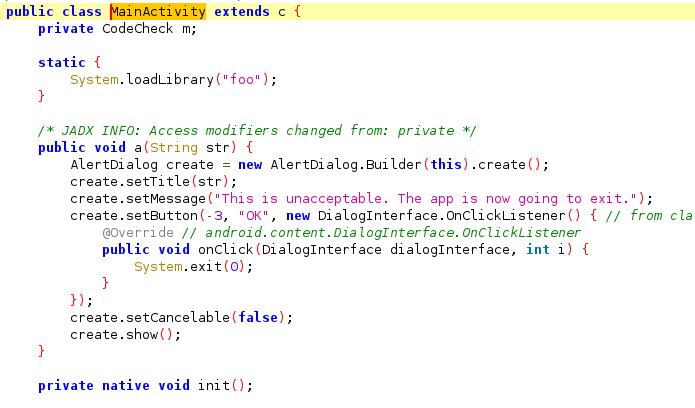
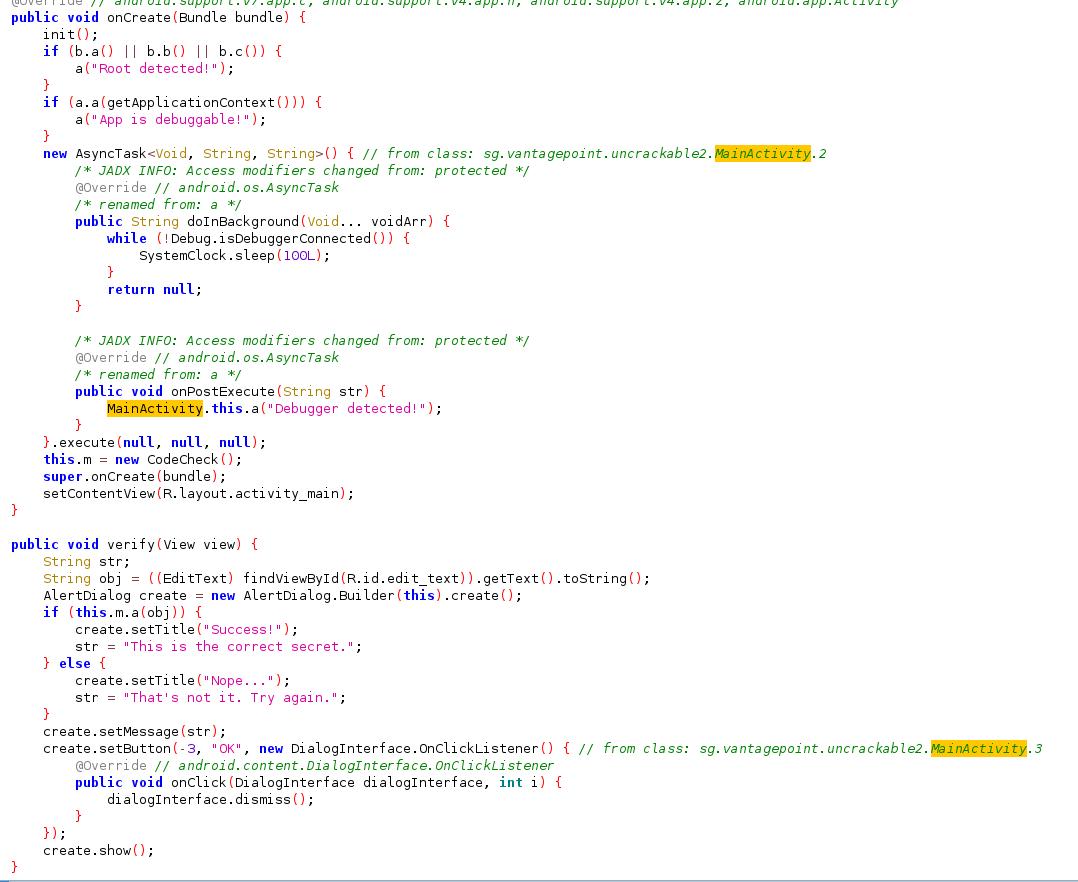
We still have an anti-root detection that’s done in onCreate and MainActivity.a. We will try to bypass it with the same method as for the first app.
There also is the verify method that probably checks the user input.
There still are a few differences here :
- The native library
libfoois loaded. - The native function
initis called at the beginning ofonCreate
Finding the secret string
This time, an instance of CodeCheck is created as m
The verify function calls m.a with the user input as argument.
Let’s see the CodeCheck class :
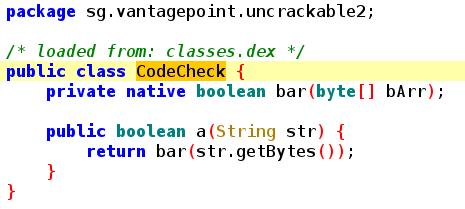
The a method calls the native function bar.
Diving into the native library
After unzipping the apk and opening the libfoo library with ida, we can try to find some information about bar.
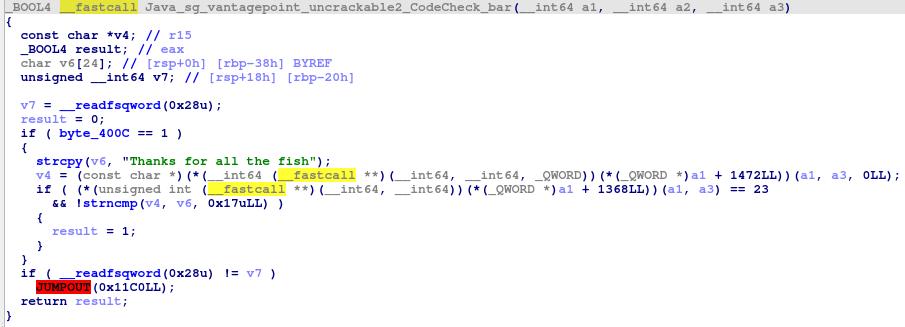
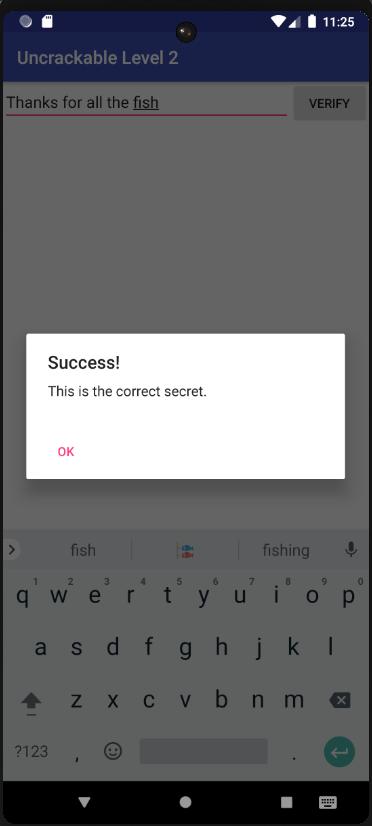
This function, most importantly, stores the string Thanks for all the fish into a variable that is then compared to the the returned value of another function.
As we are lazy efficient people, let’s assume that is the secret string.
Let’s thank for all the fish
In order to bypass the anti-root detector, we can use frida with the same script as in the first app.
Java.perform(function() {
const badMethod = Java.use("sg.vantagepoint.uncrackable1.MainActivity").a.overload("java.lang.String");
badMethod.implementation = function(str){
console.log("Bypassing MainActivity.a");
return;
//return badMethod.call(this,str);
}
});
And then after launching frida
┌──(devilsharu㉿Kali)-[~/Documents/OWASP-Mobile]
└─$ frida -U -f owasp.mstg.uncrackable2 -l uncrack2.js
Now, we can thank for all the fish !