x0rr3al?!!
This is a pretty easy rev challenge that requires a bit of script in order to be time-efficient.
We are given an ELF64 binary that takes an user input and excepts it to be the flag. We first notice that we are not able to debug it using gdb, let’s reverse it ghidra in order to understand why.
Reverse Engineering
The function names seem to obfuscated but we are able to to recognize the main function.
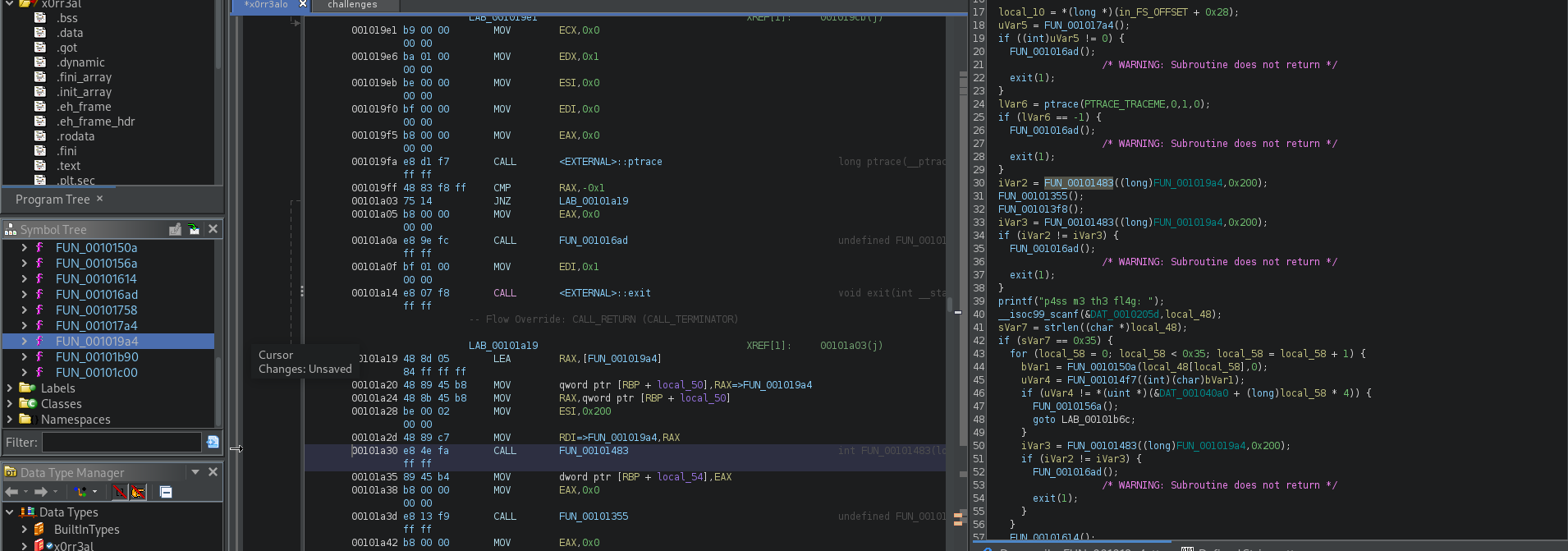
We can see that ptrace is called in order to detect if we are using a debugger. If a debugger is detected, FUN_001016adis called. However, we also notice that 2 other tests are done and may called FUN_001016ad. So, let’s patch all the tests to invert their results, so UN_001016a will never be called when using a debugger and reexport the patched binary.
We are now able to debug the binary using gdb.
Now let’s understand the rest of the program in Ghidra, we see that the input has to have a length of 53 (0x53) and the string is transformed char by char and compared to another string &DAT_001040a0 that we cannot apprehend before running the program.
Debugging with GDB
If we stop the execution of the program when the program tries to read the input, we can look at the backtrace in order to know where our main function is.
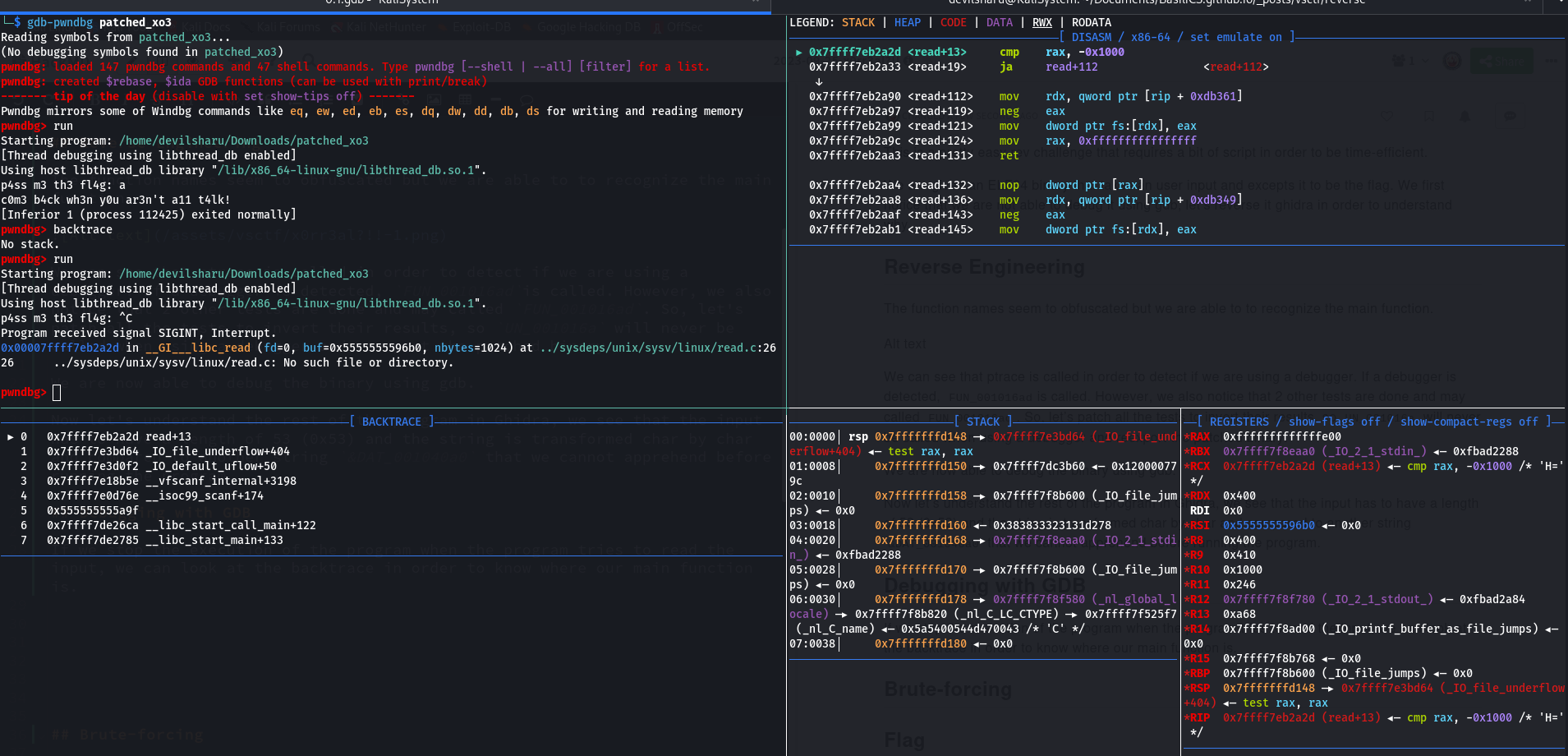
In my case, the instruction at the address 0x555555555a9f was part of the main instruction, after disassembling the instructions that were coming after, I noticed that the comparison between the transformed flag and the transformed input was happening at 0x555555555ab10
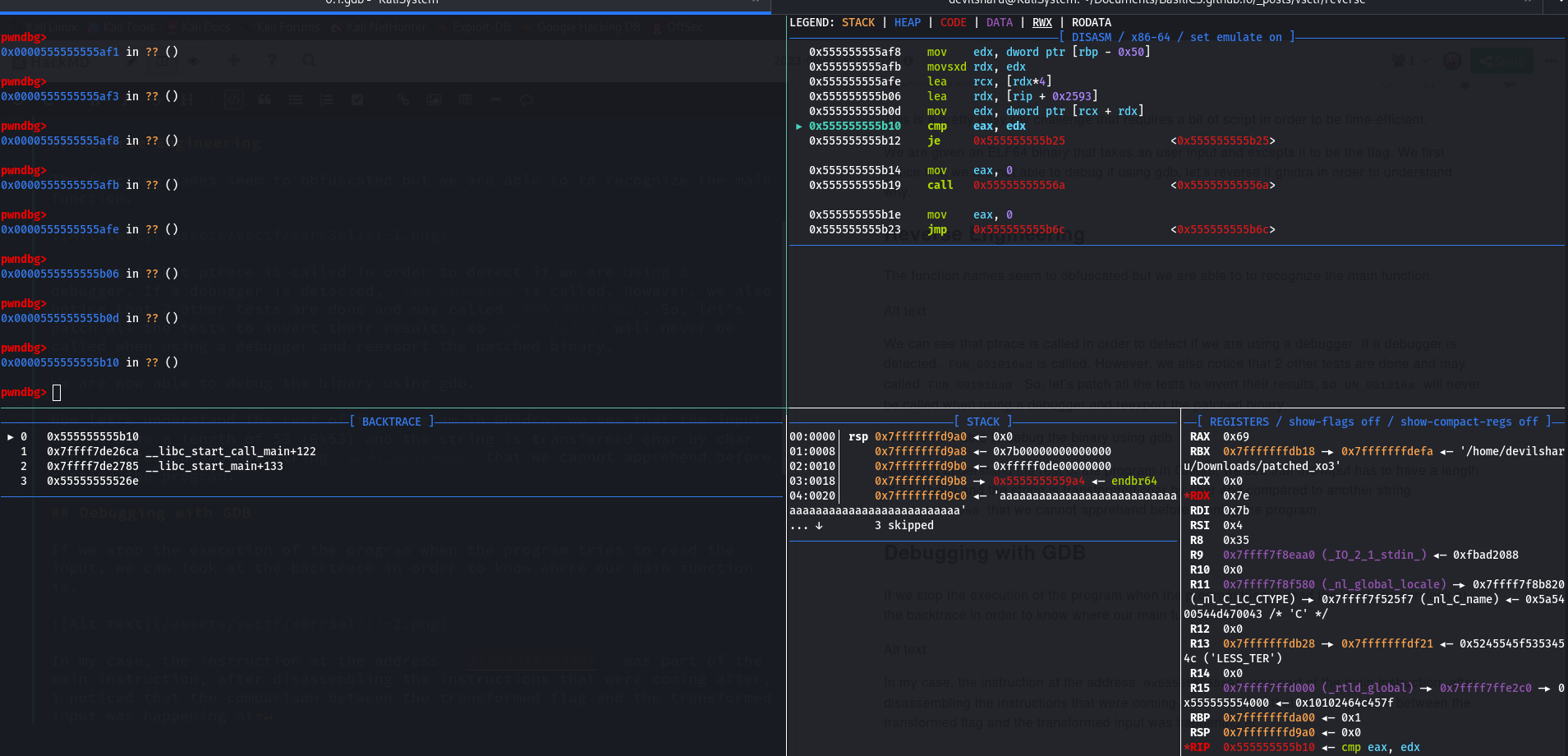
The values compared are the one stored in EAX and EDX, by changing the input we understand that our transformed input’s char is stored in EAX.
Now we only have to bruteforce the flag char by char by writing a python script for gdb which will compare both registers until finding the correct char.
Brute-forcing
The python script is the following and requires to put a unique breakpoint at the previously seen instruction
import os
import sys
import string
import time
id = 1
final = ""
source = open("x0rr3al_flag.txt","w")
S = len(string.printable)
while (id!= 54):
io = 0
for i in string.printable:
io+=1
if i in '"$&`#' or i in "');<>":
continue
flag = final+i+"X"*(53- id)
gdb.execute("run <<< "+flag )
for j in range(id-1):
gdb.execute("c")
rax= gdb.parse_and_eval("$rax")
rdx = gdb.parse_and_eval("$rdx")
if rax == rdx:
final+=str(i)
id+=1
source.write(flag+"\n")
source.close()
source = open("x0rr3al_flag.txt","a")
break
source.write(final)
Here is the content of the output file:
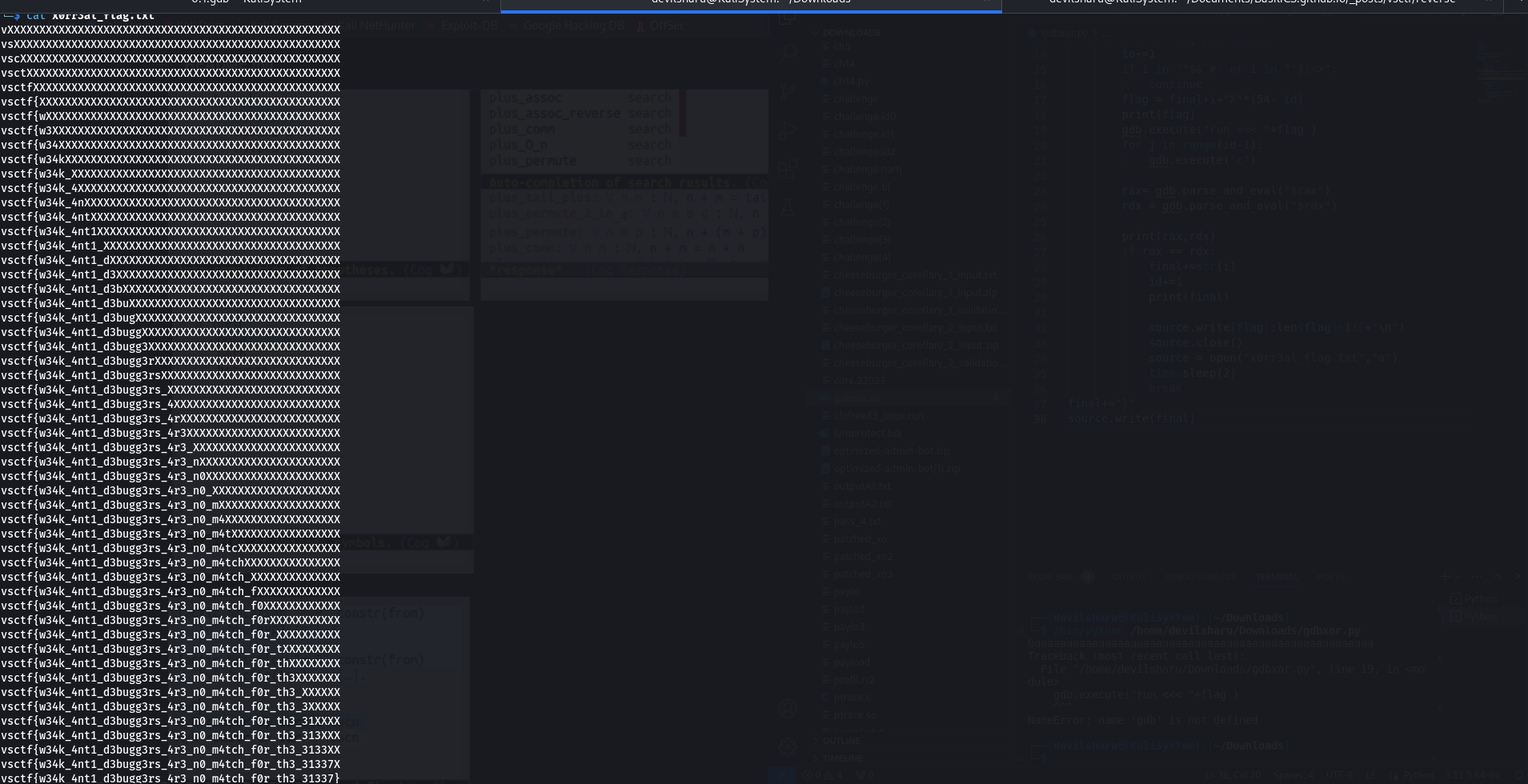
Flag
vsctf{w34k_4nt1_d3bugg3rs_4r3_n0_m4tch_f0r_th3_31337}
